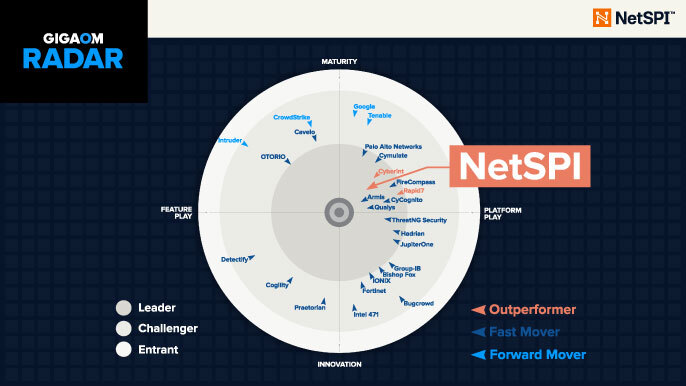
NetSPI PTaaS
Shift projects to programs with contextualized pentesting in a technology-enabled, human-delivered, platform.Application Pentesting
Secure your web, mobile, thick, and virtual applications and APIs.AI/ML Pentesting
Reduce the risk of using AI in your environment with testing and jailbreaking for LLMs.Cloud Pentesting
Secure your AWS, Azure, and Google cloud infrastructures.Blockchain Pentesting
Uncover and understand blockchain security concerns.Network Pentesting
Secure your internal, external, wireless, and mainframe networks.Secure Code Review
Find application security vulnerabilities in your source code with SAST tools and manual review.SaaS Security Assessment
Discover and remediate SaaS configuration instances and app vulnerabilities.Hardware Systems
Find vulnerabilities that could put your IoT, automotive, medical device, ATM, OT, and other cyber-physical systems at risk.Red Team
Simulate attacks to assess detection, response, and recovery capabilities across people, processes, and technology.Threat Modeling
Identify potential threats to your company’s systems and applications through a holistic program.Cybersecurity Maturity Assessment
Define prioritized steps to advance your security program.Social Engineering
Conduct email, phone, or physical security social engineering tests.
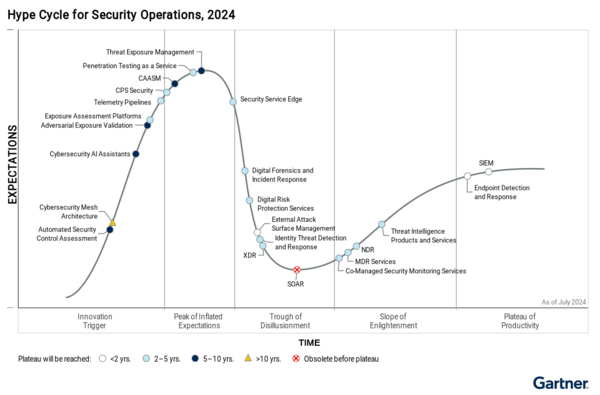
In our opinion, the Gartner® Hype Cycle™ for Security Operations, 2024 provides key insights to help organizations protect their IT systems, cloud, and digital assets by identifying threats and vulnerabilities.
Managing organizational risks was a key focus in 2024 and remains a priority for security leaders. This report states “Security operations technology and services defend IT/OT systems, cloud workloads, applications and other digital assets from attack by identifying threats, vulnerability and exposures. This Hype Cycle helps security and risk management leaders strategize and deliver SecOps capability and functions.
CTEM helps organizations improve their security posture through five recommended phases of exposure management:
Scoping
Discovery
Prioritization
Validation
Mobilization
Access the Hype Cycle to read our take aways:
Understand how to bridge gaps in your security maturity
Gain insight into technology and vendors that were recognized
Sharpen your threat detection and response efforts
Disclaimer: Gartner®, Hype Cycle™ for Security Operations, 2024, Jonathan Nunez and Andrew Davies, published July 29, 2024
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and HYPE CYCLE is a registered trademark of Gartner, Inc. and/or its affiliates and are used herein with permission. All rights reserved.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from NetSPI.