Gut Check: Are You Getting the Most Value out of Your Penetration Testing Report?

Not all penetration testing reports are created equal, so we summarized key sections to look for that build up to a comprehensive and actionable report. Quality vendors extend their reporting beyond a simple PDF and into custom software, such as The NetSPI Platform, that aids ongoing vulnerability management. Over time, the results of penetration testing engagements can be tracked, along with their severity and remediation status for simpler insight into an enterprise’s overall security performance.
Use this article and our web application penetration testing sample report to make sure reports you receive speak to prioritized findings backed up with sound methodology.
Need to find a quality penetration testing company? We’ve got you covered with this Penetration Testing RFP template.
The Anatomy of a Sample Penetration Testing Report
What’s the ultimate goal of a penetration testing report? According to our security experts, penetration testing reports have three purposes:
- Identify network, system, and application layer vulnerabilities that exist in a customer’s environment from the perspective of an unauthenticated attacker.
- Provide customers with an understanding of the potential impact vulnerabilities could have by leveraging them to gain access to critical resources.
- Provide customers with a prioritized remediation approach to address the identified vulnerabilities.
Here’s a quick rundown of what’s included in a penetration testing report.
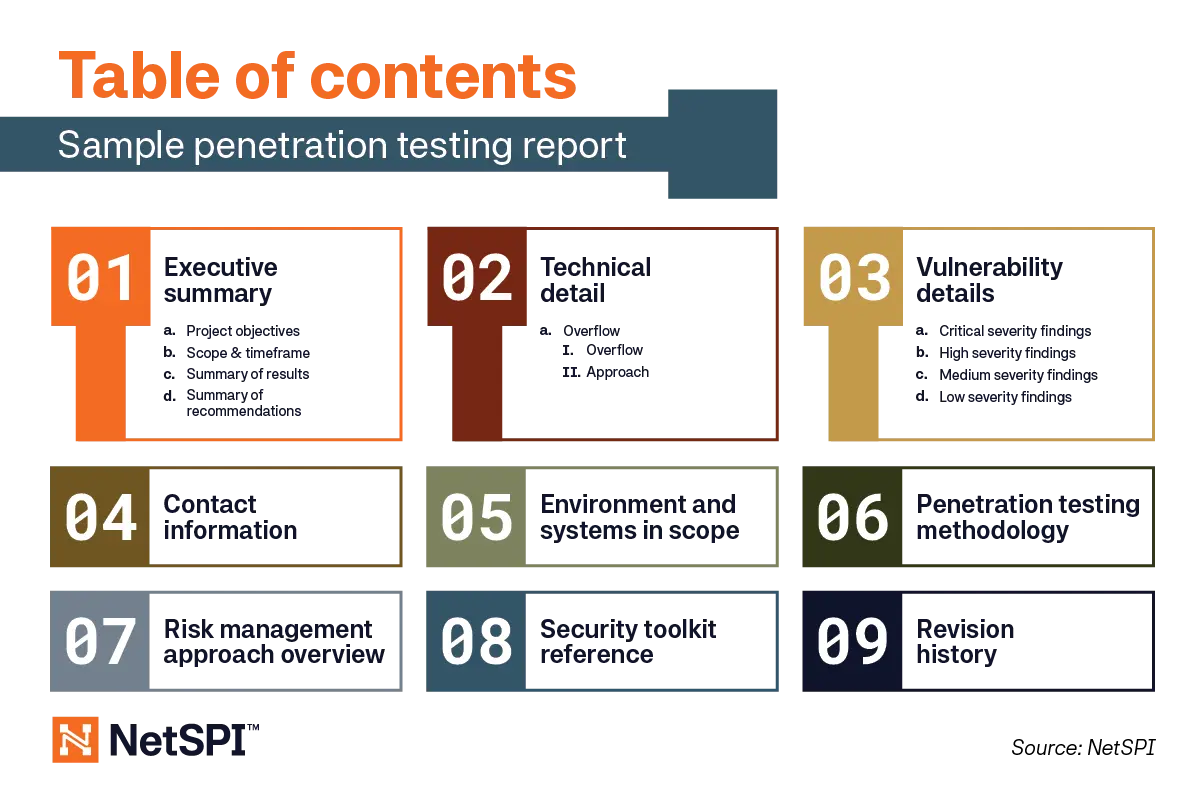
Now diving into more detail on each section.
- Executive Summary – Project objectives, scope and timeframe, summary of results, and a summary of recommendations.
- Technical Detail – A list of constraints if any are present, and the approach the penetration testers took to create the results.
- Vulnerability Details – Relevant vulnerability findings in order of priority based on risk to the business. Clients can access a list of all the report findings at any time, but the true value comes with NetSPI’s security consultants categorizing the findings into critical, high, medium, and low severity for focused remediation efforts.
- Contact Information – This is a no-brainer if you want additional support or need to pass along the report to other parties for validation.
- Environment and Systems in Scope – A list of all assets included in testing for this specific engagement.
- Penetration Testing Methodology – The steps penetration testers take when undergoing an engagement, typically covering everything from information gathering on the current network architecture, to presenting the penetration testing report.
- Risk Management Approach Overview – Communication is key to avoid unnecessary actions that could arise when undergoing a penetration test. This section overviews the steps the penetration testing company takes to proactively avoid potential emergency reactions in response to testing activities.
- Security Toolkit Reference – A list of primary tools used in the engagement. Check out this roundup of the must-have Burp extensions according to our penetration testers.
- Revision History – Finally, you’ll find a list of the people behind the engagement who helped analyze findings to create the report alongside any dates they made changes.
The level of detail and terminology varies from report to report, but the above sections make up a comprehensive penetration testing report.
Penetration Testing Report Examples
Want to get your hands on a sample penetration testing report? Take a look at NetSPI’s web application penetration testing sample report for reference. Connect with our team anytime for a gut check on the quality of penetration testing reports your receive.

Now What? Steps to Take after Receiving a Penetration Testing Report
Consider a penetration test to be a baseline of what you’re doing well and where you can find areas to improve. Conduct a post-mortem after a penetration test to review the findings and discuss a remediation plan with your team. Prioritize high-severity vulnerability findings, while tackling the subsequent categories over time.
While this report is the final deliverable following a penetration test, companies that follow a Penetration Testing as a Service (PTaaS) methodology, like NetSPI, factor these key reporting components into their pentesting platforms to track performance over time.
This leads to the growing area of continuous pentesting, which uses Attack Surface Management (ASM) to proactively monitor changes to the attack surface, paired with External Network Penetration Testing to bring a highly targeted approach to the most relevant exposures.
Whether you received your hundredth penetration test report, or you’re just starting to review your first one, benchmarking your report against NetSPI’s sample reports will give you greater context into the quality of the work in front of you. Access NetSPI’s penetration testing sample report for reference or get a second opnion on your report by contacting NetSPI.
Explore More Blog Posts
What Cybersecurity Actually Looks Like in 2026
Discover 2026’s top cybersecurity trends: AI, cloud, social engineering, and digital resilience. Stay ahead with a proactive security strategy.

Pentesting for Third-Party Risk Management: What CISOs Should Demand from Vendors
Learn why traditional third-party risk management fails and what CISOs must demand from vendors, including continuous pentesting, to manage third-party risk effectively.

Public Report: Android Quick Share Application Penetration Test
NetSPI's penetration test of Protocol X in Google Pixel 10 Pro's Quick Share Extension found one low-severity issue, now resolved. Read the full report.
