
CVE-2024-37888 – CKEditor 4 Open Link plugin XSS
At NetSPI, our mission is to uncover and mitigate security vulnerabilities before they can be exploited. This blog post explores the discovery of CVE-2024-37888, a cross-site scripting (XSS) vulnerability in the CKEditor 4 Open Link plugin. We’ll discuss the nature of this vulnerability, how it was discovered, and its implications.
What is CVE-2024-37888?
CVE-2024-37888 is a vulnerability affecting the Open Link plugin in CKEditor 4, a widely used “what you see is what you get” (WYSIWYG) editor. This flaw allows an attacker to execute arbitrary JavaScript code in the user’s browser, bypassing the library’s sanitization mechanisms. The successful exploitation of this vulnerability needs direct user interaction where an attacker can mislead/manipulate a victim into injecting code into the CKEditor workspace.
Discovered during a NetSPI client engagement, this issue was initially suspected to be an application-specific problem. Further investigation revealed that it was a previously unknown flaw in the Open Link plugin for CKEditor 4.
- Note that this vulnerability exists within the codebase of the Open Link plugin, not CKEditor 4 itself.
- Affected version: Open Link Plugin (version < 1.0.5)
- The commit containing the vulnerable code can be found here.
The Discovery Story
The journey began with a pentest of an application utilizing CKEditor 4. During testing, it was noticed that links could be clicked within the editor space, contrary to the library’s intended behavior, which prevents it from clicking/opening hyperlinks directly inside the editor space. This anomaly led to further experimentation, revealing that the “href” attribute in link tags was not being properly sanitized.
By using a payload like <a href="javascript:alert('XSS Found')">XSS</a>, a DOM XSS was triggered. Initially, it seemed this might be an existing vulnerability in the older CKEditor version in use. However, no similar CVEs were found, prompting a deeper investigation.
A custom configuration file, config.js, was discovered and examined in the client-side scripts. It contained the following lines:
config.extraPlugins = 'openlink'; config.openlink_modifier = 0; // No modifier for opening links
These lines enabled the Open Link plugin, allowing links to be opened in new tabs from the editable area. Testing with the latest versions of CKEditor 4 and the Open Link plugin confirmed that the XSS vulnerability existed even in the latest versions.
Exploitation Steps
Below are the complete prerequisites and reproduction steps for CVE-2024-37888.
Prerequisites
Reproduction Steps
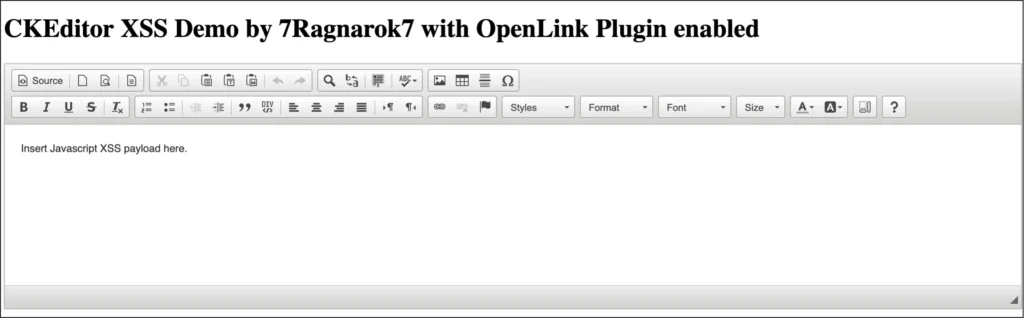
This vulnerability can be reproduced using the pre-configured CKEditor 4 instance available here: https://7ragnarok7.github.io/CVE-2024-37888/
- Insert Payload:
- Open the CKEditor instance and click on the “Source” icon.
- Insert the following payload in the text area:
<a href="javascript:alert('XSS Found')">XSS</a>
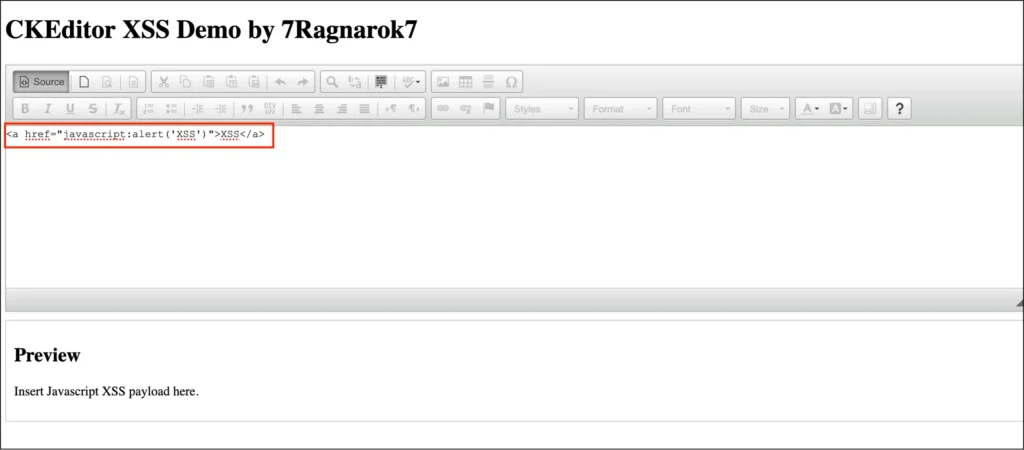
- Switch to WYSIWYG Mode:
- Click on the “Source” icon again to switch back to the WYSIWYG mode.
- Observe that the hyperlink becomes clickable inside the editor.
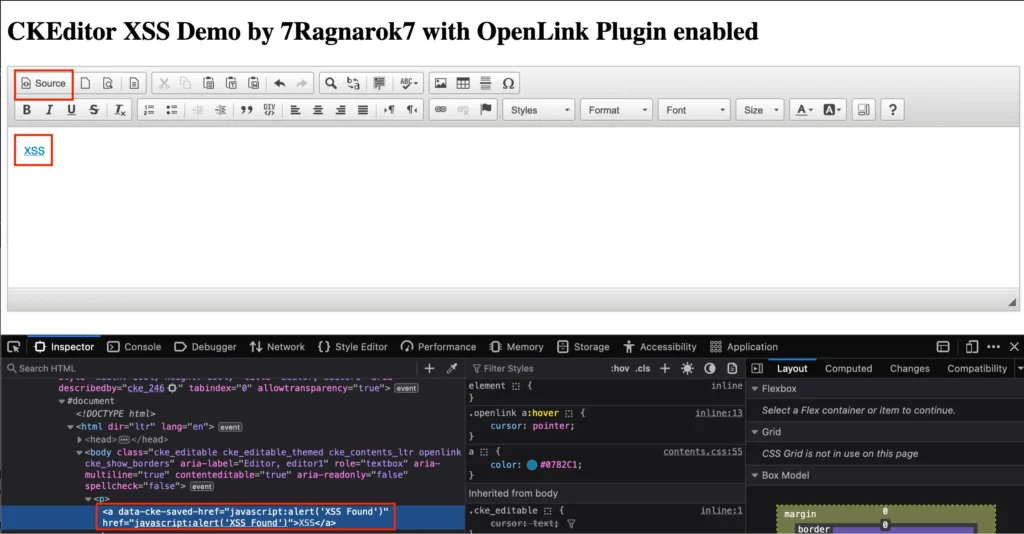
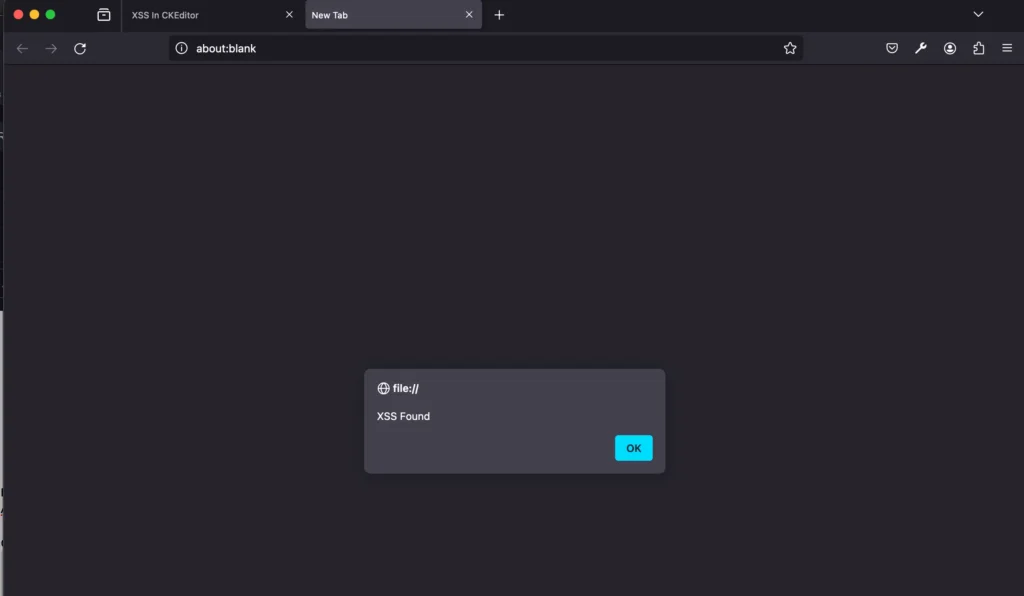
- Trigger XSS:
- Click on the hyperlink within the editor.
- Observe that the XSS payload is triggered, resulting in an alert box in a new tab.
Setup Instructions
You can set up a local instance to test this vulnerability by following these steps:
- Download CKEditor 4:
- Download the Full-Package Open-Source edition of CKEditor 4.

- Install Open Link Plugin:
- Download the Open Link plugin version 1.0.4 from here.
- Extract and place the contents into the
ckeditor/plugins/openlinkdirectory.
- Update Configuration to Include OpenLink plugin:
- Modify the
config.jsfile of CKEditor by appending the following lines to the end:
- Modify the
config.extraPlugins = 'openlink'; config.linkShowTargetTab = false; // Hide link target tab config.openlink_modifier = 0; // No modifier for opening links config.openlink_enableReadOnly = true; // Allow links to open in read-only mode
- Example
config.js:
CKEDITOR.editorConfig = function( config ) {
// Define changes to default configuration here.
config.extraPlugins = 'openlink';
config.linkShowTargetTab = false;
config.openlink_modifier = 0;
config.openlink_enableReadOnly = true;
};
- Include CKEditor in HTML:
- Ensure the CKEditor library is included in your HTML file.
<!DOCTYPE html>
<html>
<head>
<script src="path/to/ckeditor/ckeditor.js"></script>
</head>
<body>
<textarea name="editor1" id="editor1"></textarea>
<script>
CKEDITOR.replace('editor1');
</script>
</body>
</html>
Conclusion
The fix for this vulnerability is available starting with Open Link version 1.0.5. It is strongly advised that the Open Link plugin be updated to 1.0.5 or above as soon as possible.
The official advisory by the Open Link plugin maintainer can be found here.
Why Does It Matter?
This vulnerability is significant because it highlights an oversight in a widely used editor. An attacker could exploit this flaw to execute arbitrary JavaScript in the victim’s browser, leading to various malicious activities such as session hijacking, defacement, or data theft.
The discovery also underscores the importance of scrutinizing even well-established libraries and plugins. In this case, the combination of a popular editor and a lesser-known plugin created a security gap that had gone unnoticed.
The discovery of CVE-2024-37888 serves as a reminder of the ever-present need for vigilance in software security. It also emphasizes the value of thorough testing and exploration when assessing applications. For more details on this vulnerability, check out the following resources:

Authors:
Explore more blog posts

5 Essential Cybersecurity Leadership Tips for Technologists
Learn about Sam Horvath's journey from pentester to Managing Director at NetSPI, with cybersecurity leadership tips for aspiring technologists.

Hijacking SQL Server Credentials using Agent Jobs for Domain Privilege Escalation
Learn how threat actors can exploit SQL Server credential objects to escalate domain privileges and how you can detect it.
The Balancing Act of In-House vs Third-Party Penetration Testing
Discover how combining in-house and third-party penetration testing brings a hybrid approach to enhance your cybersecurity strategy.
