Tool release: AMF Deserialize Burp Plugin
Action Message Format (AMF) is one of the communication protocols used to exchange messages between Flash client and server; the others are RTMP and XML. BurpAMFDSer is another Burp plugin that will deserialize/serialize AMF request and response to and from XML with the use of Xtream library (https://xstream.codehaus.org/). BurpAMFDSer also utilizes part of Kenneth Hill’s Jmeter source code for custom AMF deserialization (https://github.com/steeltomato/jmeter-amf).
How to run:
java -classpath burp.jar;burpAMFDser.jar;xstream-1.4.2.jar burp.StartBurp
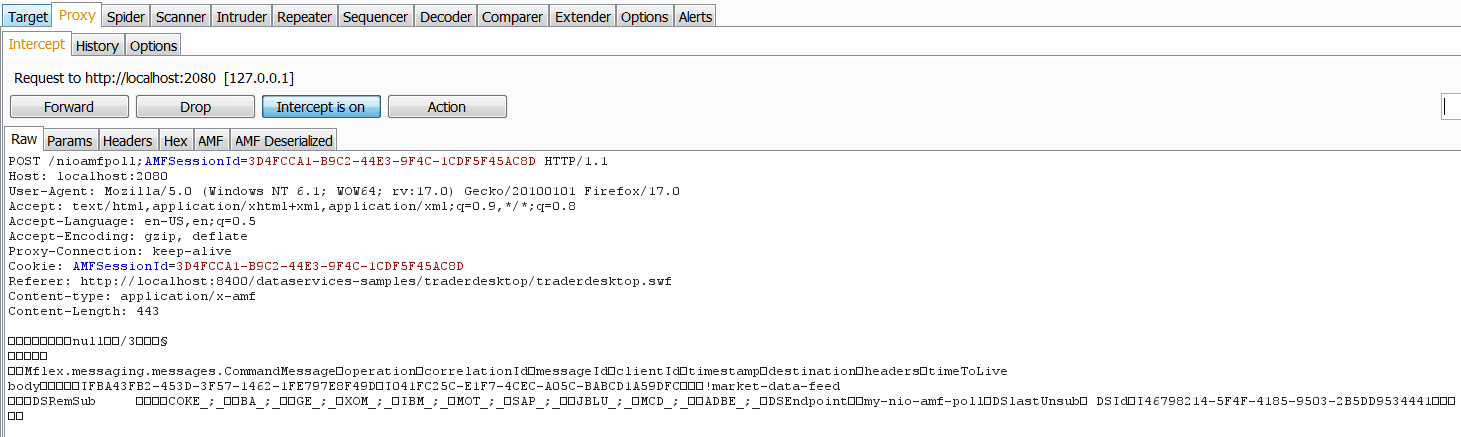
Sample serialized Request:
Sample deserialized Request:
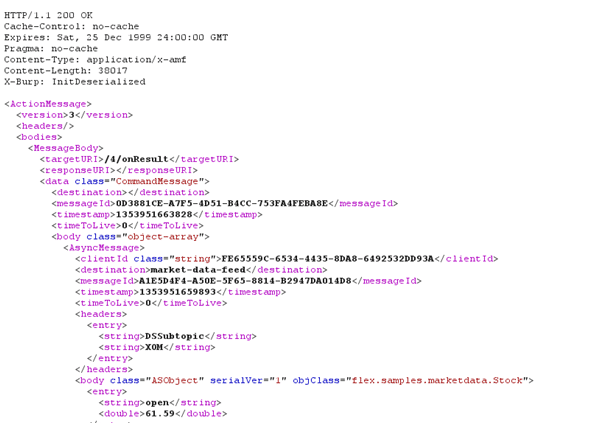
Sample deserialized Response:
Source code and executables are available at:
https://github.com/NetSPI/burp-plugins/tree/master/BurpAMFDSer/Old_APIs
The sample application in the screenshot is TraderDesktop, provided as part of ADEP Data Services for Java EE 4.6 and could be downloaded at: https://www.adobe.com/cfusion/tdrc/index.cfm?product=livecycle_dataservices
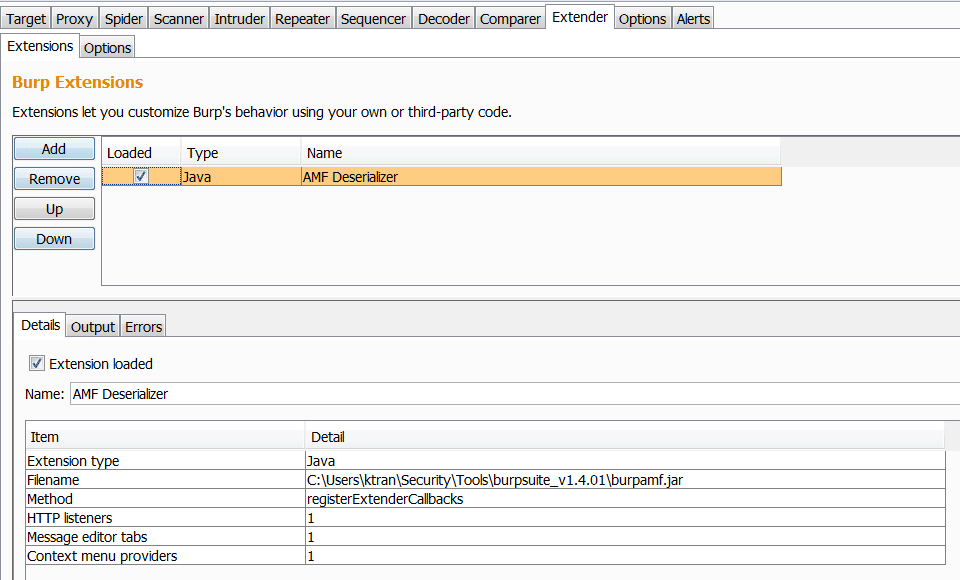
I’ve also developed a newer version of this plugin to be compatible with the new Burp Extender APIs (https://blog.portswigger.net/2012/12/draft-new-extensibility-api.html). Now you can modify AMF requests and responses in a separate tab.
The new plugin can be loaded dynamically via Burp Extender:
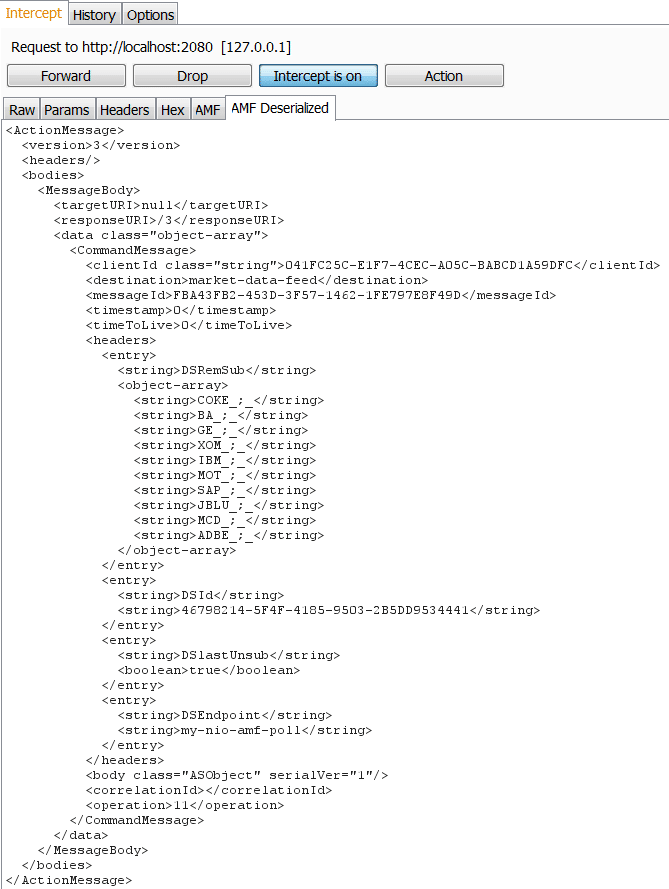
Sample Request:
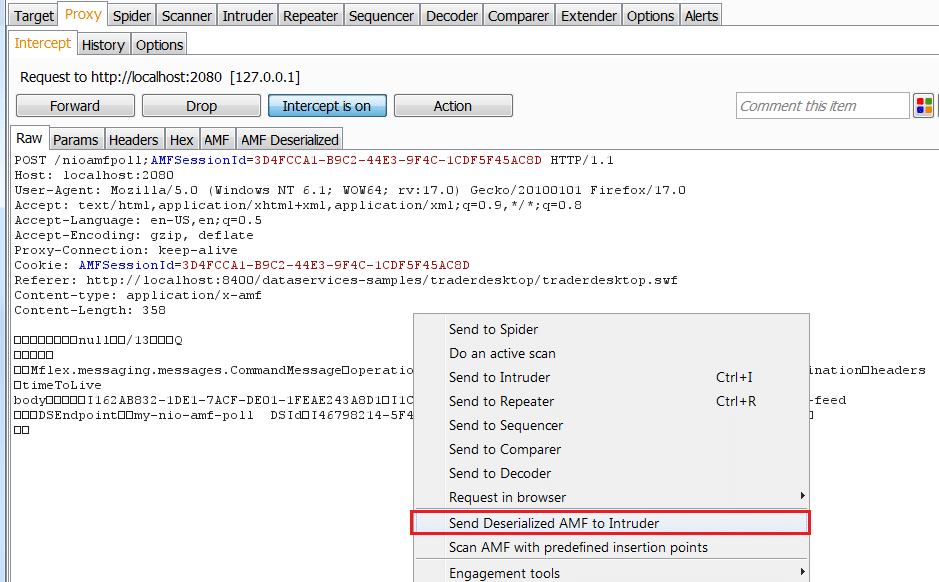
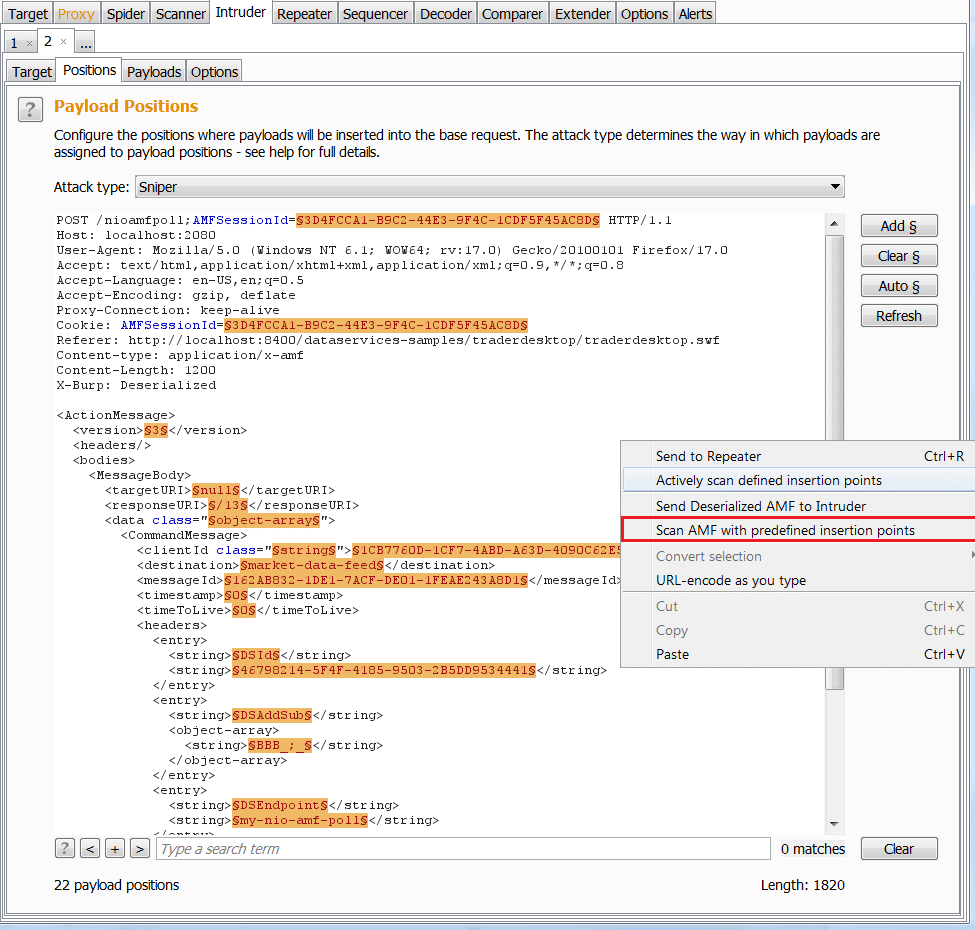
I also added 2 new menus to work with Intruder and Scanner (pro version only)
Send deserialized request to Intruder
Scan AMF (Pro version only)
Unfortunately, the new APIs are only available for Burp Suite Pro version 1.5.01 and later. Hopefully the author will update the free version soon.
If you are interested, source code and executable are available at: https://github.com/NetSPI/burp-plugins/tree/master/BurpAMFDSer/New_APIs
Explore more blog posts

Why Changing Pentesting Companies Could Be Your Best Move
Explore strategic decisions on changing pentesting companies. Balance risk, compliance, and security goals with an effective pentesting partner.

Clarifying CAASM vs EASM and Related Security Solutions
Unscramble common cybersecurity acronyms with our guide to CAASM vs EASM and more to enhance attack surface visibility and risk prioritization.
Filling up the DagBag: Privilege Escalation in Google Cloud Composer
Learn how attackers can escalate privileges in Cloud Composer by exploiting the dedicated Cloud Storage Bucket and the risks of default configurations.