Cracking Stats for Q3 2014

During many of our penetration tests, we gather domain password hashes (with permission of the client) for offline cracking and analysis. This blog is a quick summary of the hashes that we attempted to crack in the third quarter of 2014 (and so far for this year). The plan is continue doing this again at the end of the year to see how we did overall for the year (three quarters down, one to go). Please keep in mind that this is not an all-encompassing sample. We do not collect domain hashes during every single penetration test, as some clients do not want us to.
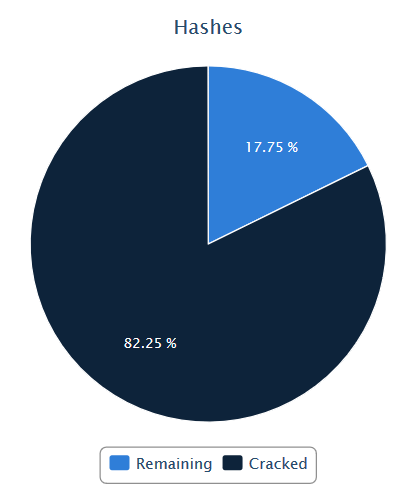
The sample for this quarter included three sets of domain hashes that added up to 26,692 hashes. Two of the three sets had some LM hashes stored along with the NTLM hashes, but none of the LM stored passwords were that complicated. Just like last quarter, it wasn’t a huge advantage. Of the hashes, 11,776 were duplicates, leaving 14,916 unique hashes. Of the 26,692 hashes, we were able to crack 21,955 (82.25%).
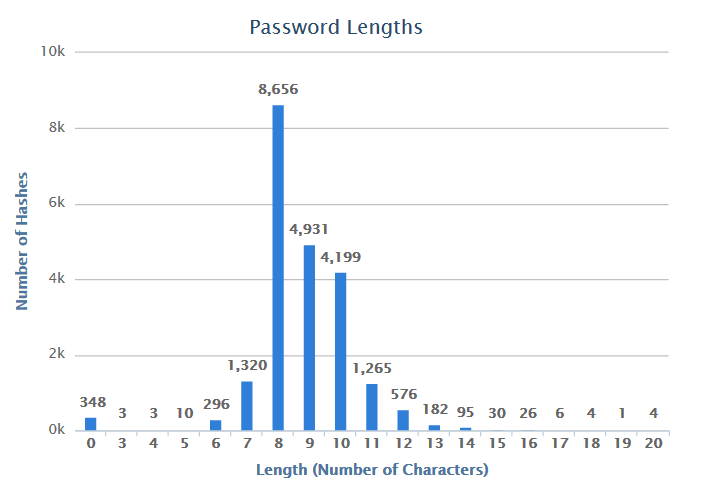
Cracked Password Length Breakdown:
As you can see, the cracked passwords peak at the eight character length. This is pretty common for a minimum password length, so it’s not a big surprise that this is the most common length cracked. It’s also been the peak every quarter this year. It should also be noted that since we’re able to get through the entire eight character keyspace in about two and a half days, which may be influencing the peak.
Some interesting finds:
- Most Common Password (1120 instances): A Client Specific Default Account Password
- Longest Password: jesusitrustinyou@123 (20 characters)
- Most Common Length (8,656 instances): 8 characters
- Instances of “Summer2014”: 394
- Instances of “Spring123”: 300
- Instances of “Summer123”: 262
- Instances of “Summer14”: 163
- Instances of “password” (full word, case-insensitive): 251
- Blank passwords: 348
- Top mask pattern: ?u?l?l?l?d?d?d?d?s (1,415 instances)
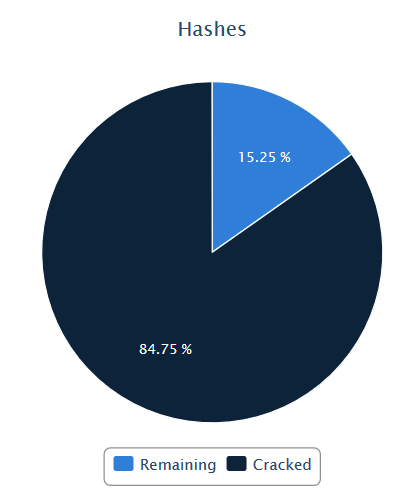
So far this year, we’ve collected 60,638 hashes to crack. Of those, we’ve been able to crack 51,393 (84.75%).
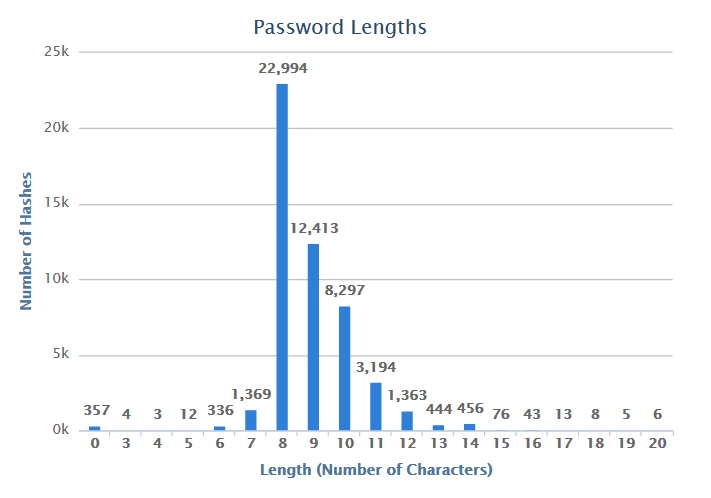
Here’s the length breakdown for the year, so far.
Some more interesting finds:
- Most Common Password – (that we can print here): Password1 (1410 instances)
- Longest Passwords: Six different passwords were 20 characters
- Most Common Length (22,994 instances): 8 characters
- Instances of “password” (full word, case-insensitive): 2,926
- Instances of “SEASON2014”: 1,404
- -SEASON = spring, summer, fall, winter (case-insensitive)
- Top Mask Pattern: ?u?l?l?l?l?l?d?d (3,068 instances)
I put together an hcmask file (to use with oclHashcat) of our top forty password patterns that were identified for this quarter. Additionally, I put together one for everything that we’ve cracked for the first half of the year. You can download them here – Q3 Hcmask File – Q1,Q2,Q3 Hcmask File. I plan on wrapping this up next quarter, so check back to see how this mask files have changed and to see how well we’ve done across the year.
For more information on how we built our GPU-enhanced password cracking box, check out our slides.
For a general outline of our password cracking methodology check out this post.
Explore More Blog Posts

Why Security Leaders Can’t Ignore macOS Anymore
With rising macOS threats, many security controls fail. Learn how to validate your detective controls and close the Mac detection gap to mitigate business risk.

Turning Regulation into a Resilience Advantage: 6 Top Pentesting Tips for CISOs
Regulations and cyber threats are moving at breakneck speed. And so are expectations from boards, regulators, and auditors. For today’s CISOs, the real question isn’t “Are we compliant?” it’s “Are we resilient?”

Webinar Recap: How to Keep Your CISO Out of Jail
Learn how CISOs can reduce legal risk by documenting decisions, fostering security culture, and aligning cybersecurity with business goals.