6 Breach and Attack Simulation Use Cases That Enhance Your Cyber Resilience
TL;DR
The breach and attack simulation (BAS) market is projected to experience substantial growth over the next several years. As the market grows, it’s important to understand that breach and attack simulation offers more than security control validation. Breach and attack simulation tools also support business use cases, including strategic security planning, demonstrating ROI, optimizing red team exercises, and supporting continuous threat exposure management.
Introduction
The breach and attack simulation (BAS) market is expected to experience substantial growth, with a projected compound annual growth rate of 33.4% between 2022 and 2029, reaching nearly $35 billion in 2029.
To better understand why this is a booming market, it is important to recognize breach and attack simulation use cases, and how tools like NetSPI Breach and Attack Simulation can help enhance security posture, promote continuous threat exposure management (CTEM), and support executives with cybersecurity strategy and planning.
Security Control Validation and Defense Readiness
Organizations continue to heavily invest in their security tech stack to defend against the evolving cyber threat landscape. They are investing in tools such as EDR, SIEM, SOAR, and XDR, and often implement them with out-of-the-box, inadequate, or outdated settings.
NetSPI’s security experts validate this challenge, finding that nearly 75% of common attack behaviors are missed by EDR, SIEM, and MSSPs.
To be effective, security teams should tailor security detection controls to their unique environment.
Security teams should test the effectiveness of their tech stack’s security controls through security control validation. This uses common tactics, techniques, and procedures (TTPs) to simulate real-world threats and evaluate whether security controls are implemented and functioning as intended by the security vendor.
By identifying detection control gaps, organizations can fine-tune security controls and continuously validate them with automated tests. This proactive approach allows security teams to optimize detection controls, strengthen security coverage, and improve detection across the cybersecurity kill chain.
Detect Ransomware Earlier
Ransomware attacks continue to threaten businesses worldwide, and 59% of organizations reported ransomware hits in 2023. To stay ahead of ransomware, early detection and improved detection capabilities are essential to stop intrusions from escalating into full-scale attacks.
BAS tools enable organizations to mimic TTPs, patterns, and behaviors that specific ransomware operators use to assess their ransomware detection capabilities and refine their defenses. By regularly testing and adjusting security controls, companies can reduce the risk of ransomware intrusions and enhance their resilience.

Continuous Threat Exposure Management
CTEM is a proactive security framework designed to reduce exposure to cyber threats and prevent large-scale cyberattacks.
According to Gartner by 2026, “…organizations prioritizing security investments based on a CTEM program will realize a two-thirds reduction in breaches.”
CTEM consists of five stages: scoping, discovery, prioritization, validation, and mobilization. BAS tools play a pivotal role in the validation phase, offering continuous assessment of detection controls. This capability strengthens an organization’s defense against evolving threats, providing detailed prevention guidance and continuous testing capabilities.

Strategic Planning and ROI
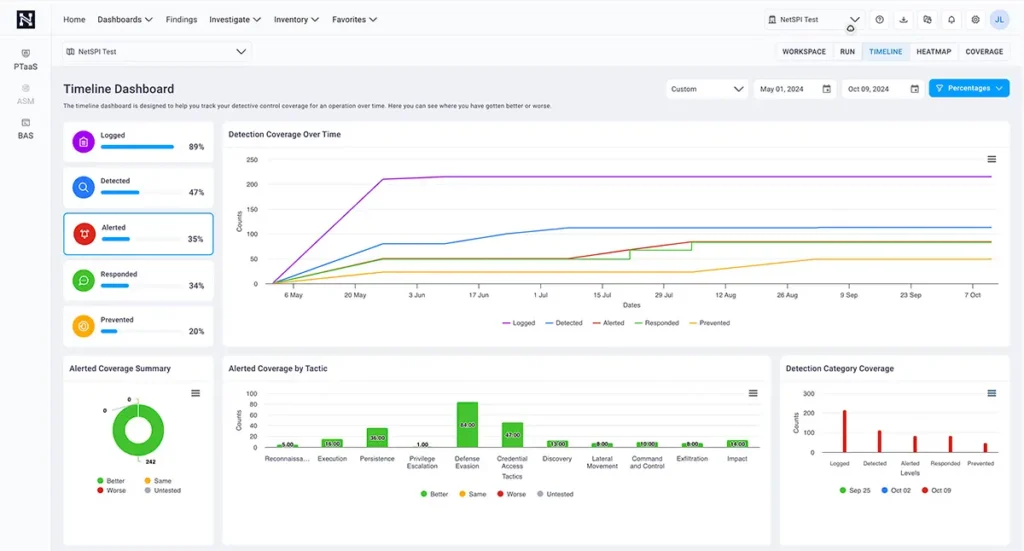
BAS tools are invaluable for strategic planning, providing insights that help justify security investments. Most BAS solutions offer visualizations and reports of security coverage that demonstrate return of investment, and can be used in discussions with stakeholders about cybersecurity priorities.
NetSPI Breach and Attack Simulation offers additional features to help security leaders with strategic planning, such as a heat map in a traditional MITRE ATT&CK matrix that highlights areas needing improvement, detailed prevention guidance, a timeline to demonstrate improvement over time and prove your security investments are producing measurable results, and a comparison of security vendors’ detection capabilities.
With NetSPI BAS, organizations can make informed decisions, optimize spending, and improve their security strategy.
Red, Blue, and Purple Team Exercises
BAS solutions can complement and maximize the testing capabilities of red, blue, and purple team exercises. BAS tools can automate some processes of testing detection control capabilities and provide real-time insights into coverage within an organization’s network.
This capability complements the efforts of red team operations, which are typically tasked with manual penetration testing and strategic attack planning.
By leveraging BAS tools, red teams are equipped with valuable data-driven insights that highlight areas of risk, allowing them to focus their expertise on more complex security challenges.
NetSPI BAS offers flexibility for advanced users like red teams, enabling the customization and automation of tests, and advanced test capabilities. It also features detailed analytics and reporting, educational resources, thorough test details of specific TTPs, self-running instructions, and remediation steps.
BAS Vendor Comparison
Benchmarking and comparing the performance of tools in the security stack is a unique use case that NetSPI Breach and Attack Simulation offers. The vendor comparison feature provides a side-by-side analysis of the tools we’re able to detect and unable to detect during tests. This information supports vendor selection during proof of concept (POC) or proof of value (POV) stages, and guides decisions regarding the need for additional or reducing tools.
The vendor comparison feature empowers organizations to make informed decisions about their security investments, aligning them with their unique needs and objectives. It highlights the detection capabilities of each vendor, facilitating strategic planning and budget allocation.
Strengthen Your Defenses with NetSPI Breach and Attack Simulation
Breach and attack simulation tools provide organizations with more than just a method to test and enhance their security detection capabilities. They also support strategic security planning, demonstrate ROI, optimize red team exercises, and enable CTEM programs. As these use cases evolve alongside the changing threat landscape, the BAS market is poised for consistent growth year after year.
Elevate your cybersecurity strategy by accessing the Ransomware Detection Checklist to strengthen your ransomware detection efforts.
Explore more blog posts

Exploiting Second Order SQL Injection with Stored Procedures
Learn how to detect and exploit second-order SQL injection vulnerabilities using Out-of-Band (OOB) techniques, including leveraging DNS requests for data extraction.

CTEM Defined: The Fundamentals of Continuous Threat Exposure Management
Learn how continuous threat exposure management (CTEM) boosts cybersecurity with proactive strategies to assess, manage, and reduce risks.

Balancing Security and Usability of Large Language Models: An LLM Benchmarking Framework
Explore the integration of Large Language Models (LLMs) in critical systems and the balance between security and usability with a new LLM benchmarking framework.


