
Intercepting Native iOS Application Traffic
In this blog, we will go through proxying an iOS application which uses native web sockets to interact with a web server. The blog will help penetration testers who are trying to intercept sensitive data that is being sent by an iOS application in a non-trivial manner over the network because some applications do not respect the iOS proxy settings.
During a recent iOS application penetration test, I encountered an iOS application that was sending data to port 20xx on a web server. This application traffic could not be proxied by changing the iOS manual proxy settings located at (Settings -> Wi-Fi -> HTTP Proxy -> Manual) and forwarding the iDevice traffic to the proxy. One of the reasons that the normal proxying method might be failing is because it might be using some native websockets to interact with the web server instead of the normal UIWebView class. For more technical details of how websockets in native iOS can be configured, check out this elabs blog post.
There is a workaround to fix this problem. We can perform DNS spoofing to forward all the HTTP traffic for all of the ports through a MitM proxy like Burp. The blog is divided into three main steps.
- Sniff traffic using Wireshark to find out the port and IP of the webserver.
- Spoof the DNS for the iDevice to send all data to laptop.
- Start a proxy on the laptop to intercept traffic all traffic from iDevice after DNS spoofing.
Given below is a step by step approach to intercept Native Web Socket iOS application traffic.
- Create a wireless hot spot with your machine and connect the iDevice to the hotspot. [Note the machine needs to be connected to Ethernet or some other route out to the internet as the Wi-Fi interface will be used for the hotspot. Refer here for information on how to create a hotspot on a windows machine]
- Start a network sniffer (like Wireshark) and look for traffic going to any non-standard ports.
- Filter the traffic to look at the traffic going to the destination server IP (ip.dst== ip.ip.ip.ip)
- Note the port number where the traffic is being sent.
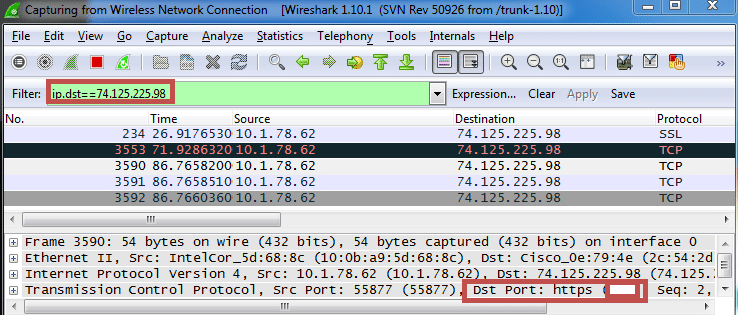
Fig 1: Finding the non-standard port number where application sends Traffic.
- Start the Metasploit console to perform DNS spoofing and enter the following commands.
- Search fakedns
- use auxiliary/server/fakedns
- set SRVHOST = (IP address of laptop which is running the hotspot)
- set SRVPORT = 53, set TARGETACTION = BYPASS, set TARGETDOMAIN = www.apple.com (Note: by setting TARGETDOMAIN= www.apple.com, all the traffic except the traffic coming from apple.com will be spoofed)
- set targethost = (IP address of laptop which is running the hotspot)
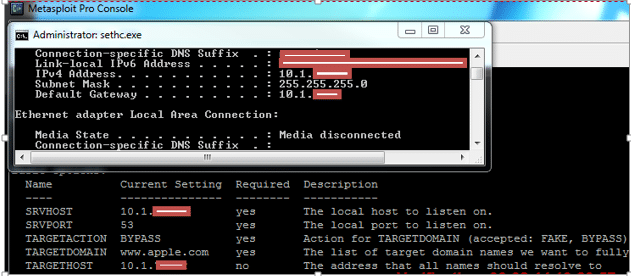
Fig 2: Configuring DNS server on the laptop using fakedns module in Metasploit.
- Configure Burp to listen on specific ports for the incoming traffic from iDevice and forward it to the appropriate port as follows:
- Go to Proxy’Options’Add; set ‘bind port’ to the port where the traffic needs to be sent (note: this is the non-standard tcp port number recorded in Wireshark)
- Listen on all interfaces
- Click Request Handling’ Redirect to host: (Enter the domain name of the server)
- Request Handling ‘ Redirect to port: (Enter the corresponding port number)
- Click force use of SSL if the outgoing traffic is sent using https.
- Click ok and repeat the above steps for all the ports that the iOS application is explicitly sending HTTP application traffic to. In other words, every port will require a separate Proxy listener to be configured in burp.
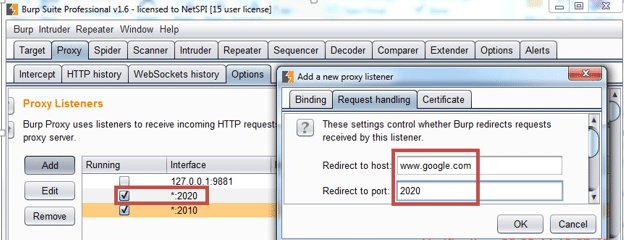
Fig 3: Configure incoming listener and redirect the iDevice traffic to appropriate IP and port to Server.
- Configure Proxy settings in iDevice:
- Click settings ‘ Wi-Fi ‘Click on hotspot ‘ DHCP and set DNS = (IP of Laptop)
- Set HTTP Proxy to the IP address of the laptop and corresponding port in burp. (this is the normal setting to proxy standard HTTP traffic)
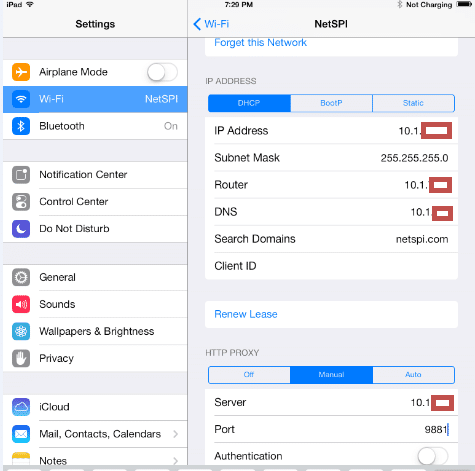
Fig 4: Configure IP and DNS forwarding settings in the IOS device.
- Type “exploit” in the Metasploit console and you will see the application traffic been proxied for non-standard ports in burp.
This small tweak can be used to overcome the problem of proxying non-trivial iOS application traffic.
Explore more blog posts
Celebrating NetSPI’s Partners of the Year 2024
Congratulations to NetSPI’s 2024 Partner of the Year Recipients Defy Security, VLCM, Softcat, Enduir, Evotek, and AWS

Exploiting Second Order SQL Injection with Stored Procedures
Learn how to detect and exploit second-order SQL injection vulnerabilities using Out-of-Band (OOB) techniques, including leveraging DNS requests for data extraction.

CTEM Defined: The Fundamentals of Continuous Threat Exposure Management
Learn how continuous threat exposure management (CTEM) boosts cybersecurity with proactive strategies to assess, manage, and reduce risks.