
Explore the Minds of The NetSPI Agents
Advance your proactive security knowledge by learning from some of the brightest people in cybersecurity. Our executive blog gives perspective on industry trends, while Hack Responsibly dives deep into the latest CVEs and tactical approaches our team takes. Take your pick!
Our Favorite Picks

CVE-2024-21378 — Remote Code Execution in Microsoft Outlook
Learn how NetSPI discovered that Microsoft Outlook was vulnerable to authenticated remote code execution (RCE) via synced form objects.
15 Ways to Bypass the PowerShell Execution Policy
NetSPI security expert Scott Sutherland covers 15 ways to bypass the PowerShell execution policy without having local administrator rights on the system.

How to Use Attack Surface Management for Continuous Pentesting
Uncover attack surfaces and exposures with NetSPI’s offensive security including Attack Surface Management (ASM) to enable continuous pentesting.
What Cybersecurity Actually Looks Like in 2026
Discover 2026’s top cybersecurity trends: AI, cloud, social engineering, and digital resilience. Stay ahead with a proactive security strategy.

Pentesting for Third-Party Risk Management: What CISOs Should Demand from Vendors
Learn why traditional third-party risk management fails and what CISOs must demand from vendors, including continuous pentesting, to manage third-party risk effectively.

Public Report: Android Quick Share Application Penetration Test
NetSPI’s penetration test of Protocol X in Google Pixel 10 Pro’s Quick Share Extension found one low-severity issue, now resolved. Read the full report.
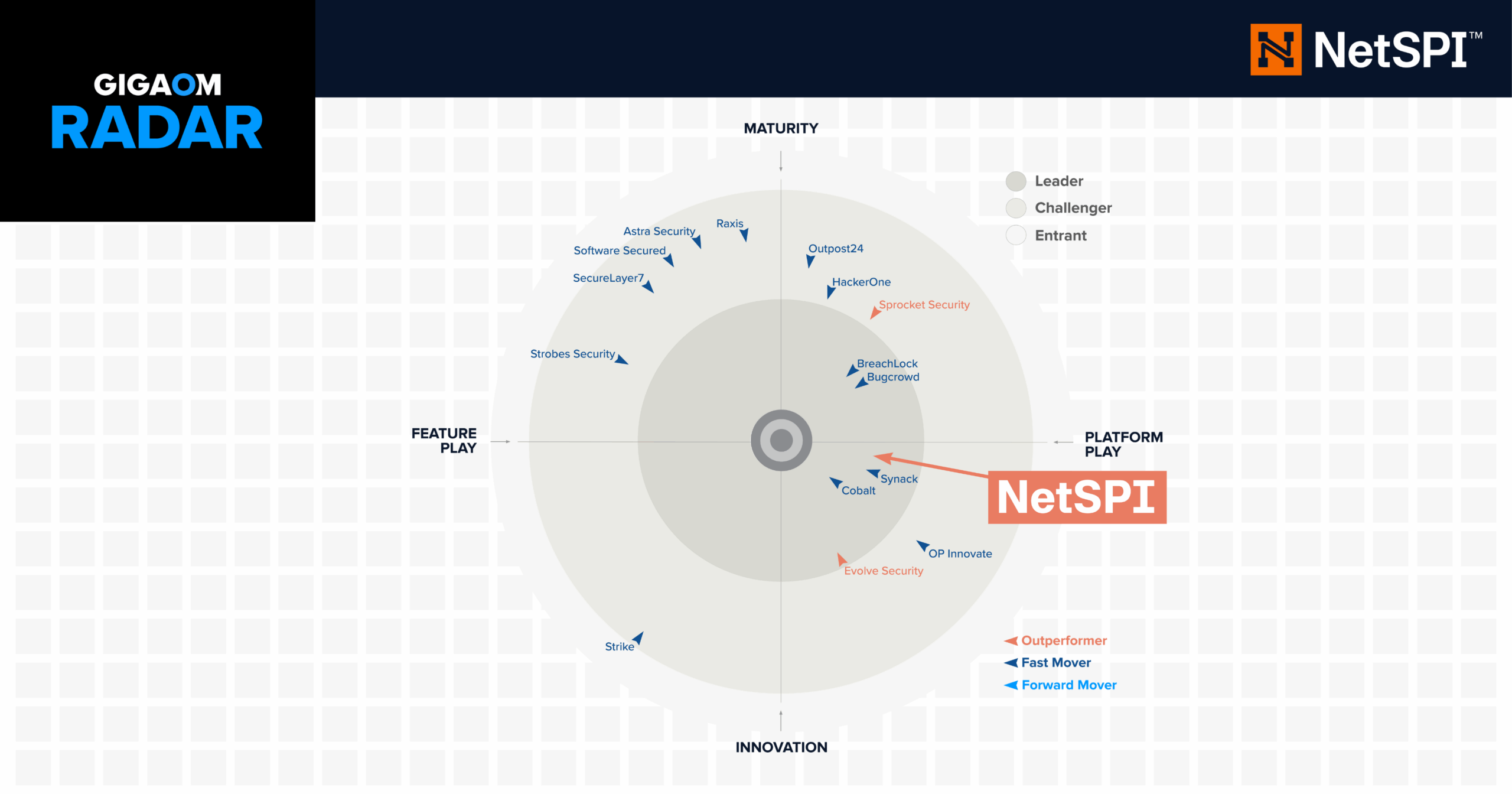
Navigating the PTaaS Market with the GigaOm Radar Report
Explore the GigaOm Radar for Penetration Testing as a Service (PTaaS) to see why NetSPI was named a Leader and Outperformer.

Why Security Leaders Can’t Ignore macOS Anymore
With rising macOS threats, many security controls fail. Learn how to validate your detective controls and close the Mac detection gap to mitigate business risk.

Turning Regulation into a Resilience Advantage: 6 Top Pentesting Tips for CISOs
Regulations and cyber threats are moving at breakneck speed. And so are expectations from boards, regulators, and auditors. For today’s CISOs, the real question isn’t “Are we compliant?” it’s “Are we resilient?”

Webinar Recap: How to Keep Your CISO Out of Jail
Learn how CISOs can reduce legal risk by documenting decisions, fostering security culture, and aligning cybersecurity with business goals.

Decrypting VM Extension Settings with Azure WireServer
The Azure WireServer service provides configuration data to Azure Virtual Machines. Join us as we walkthrough the process of decrypting that data to find sensitive information.

How App Integration Transactions Increase the Attack Surface of LLMs
Learn how OpenAI’s AppsSDK, AgentKit, and “Buy It” turn LLMs into transactional agents—expanding security risks from rapid rollout, prompt injection, and access control gaps.

API Security Testing: The Overlooked Frontline in Application Penetration Testing
In this article, NetSPI Managing Director Nate Brown, highlights the importance of securing APIs to protect against cyberattacks and data breaches.

Webinar Recap: Everything You Wish You Didn’t Have to Know About Ransomware
Learn about the evolving ransomware landscape, including how attackers operate, the roles within the ransomware economy, and actionable strategies to strengthen your defenses.

6 Security Trends Every CISO Should Know
Discover top security trends from AI governance to Zero Trust. Explore actionable insights tailored to help CISOs strengthen defenses.
