Overview
Trust within a business is critical, especially when building an effective security program. But how do security leaders establish trust and keep it?
Join offensive security professional, Phil Morris and NetSPI’s Chad Peterson as they share lessons learned and expertise from their tenured careers in security leadership. They will provide you with practical steps on how to:
- Build a security champions team across silos
- Create shared goals and responsibilities
- Develop a risk-aware security program
Establishing and keeping trust when it comes to security isn’t simple, but it’s also not as complex as some may think. During this webinar, learn to secure what makes sense, add compensating controls where needed, and understand the roles security versus the business take when managing risk.
Key highlights:
- 0:50 – Introductions
- 2:43 – What is trust?
- 3:33 – The Cynefin framework
- 7:35 – Three requirements for establishing trust
- 17:30 – Build a security champions team across silos
- 24:12 – Develop a risk-aware security program
- 32:33 – How do you keep trust?
What is trust?
Trust is saying to your partners, colleagues, or senior management that we have shared values, and we have a shared vision. The underlying theme of everything we talk about in this webinar is that you can’t do this alone. Security healthcare is a complex collaborative business. Establishing trust is important for your career and important for all the projects you work on going forward.
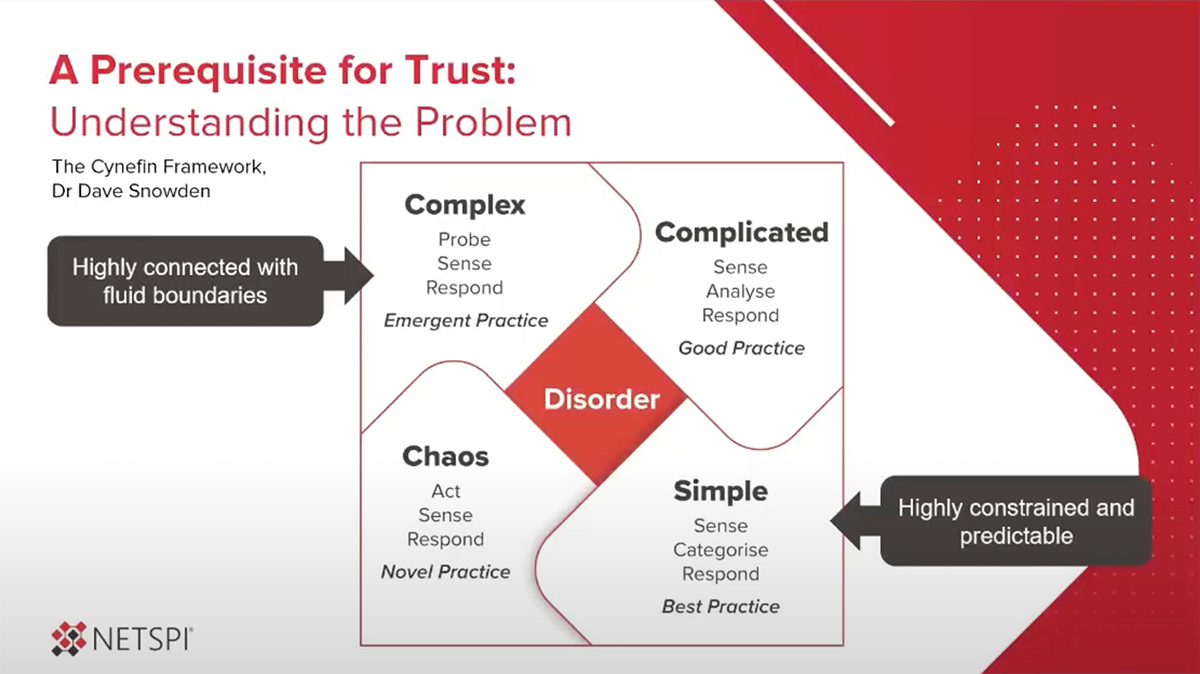
The Cynefin Framework
To get started, it’s important to introduce a framework called the Cynefin framework to help understand the different types of problems we’re wrestling with when it comes to trust. This framework was designed by Dr. David Snowden several years ago when he was working with IBM Global Services. It’s evolved over the years to be one of the leading frameworks to help comprehend how you can understand what world you’re living with, what sort of problem you’re dealing with, and how to respond to the situations you see there.
The framework is broken down into four domains, including:
- Chaos: In the chaos domain, you need to do anything possible to get out of a situation as soon as possible, then work through the next steps. One example that would represent this domain is if a house is on fire, get everyone out then work on the next steps.
- Simple: In the simple domain, there are established best practices you can follow to solve the problem. There is a clear connection between the cause and effect needed to achieve the desired outcome. A lot of command-and-control management schemes work in this domain.
- Complicated: In this space, good practices are available to follow, but not one defined best practice. If you’re in the complicated space, the right way to approach this is to sense what your options are, analyze perspectives, and respond, then course correct over time. A lot of agile methodologies are based on operating in the complicated space where you don’t quite know the outcome you’re shooting for yet, but you can sense where you need to go. Some of the work in security is in the complicated space.
- Complex: Most of the work in healthcare, and almost all of the work in security is in the complex realm. There are a lot of fluid boundaries, there’s a lot of vagueness in this domain. The hardest projects often involve working with senior leadership, to establish trust and credibility. In a complex space, senior leadership may not be able to see it as something simple. If you’re in the complex domain, you have to experiment and try some approaches because what works for one company doesn’t work for the other.
With Cynefin as a framework for understanding how everybody needs to be on the same page, it’s important as a subject matter expert, IT professional, or senior manager to recognize when the other people that you’re working with may not see the world from that perspective.
3 requirements for establishing trust
The Cynefin framework can be used to build on some common best practices to establish trust in your business.
Three key requirements for establishing trust in any business include:
- Understand the business: This encompasses knowing your products and services, learning your markets and competitors, and clarifying your priorities and processes (and who owns specific processes).
- Speak the language of the executives: This involves recognizing that senior executives are looking at the business from the context of risk postures and options for differentiation, or options for managing and leveraging resources. Executives share priorities and what the risk tolerance is for managing certain types of priorities. And the priorities trickle down to mid-level managers or other operators who from there, take them down to the implementation and operations teams. It’s important to speak to executives in the context of risk and challenges. When you’re working with different levels of executives in a complex organization, you need to be able to shift and speak different dialects of the business according to the specific audience.
- Become a good negotiator: Being a good negotiator means knowing your style and the negotiation style of others. Negotiation styles can often be broken down into three categories, including:
- The Analyst
- Usually very prepared
- Hesitant to give up things
- Appreciate data, so using data when negotiating with the analyst stile is key
- Weakest pairing is with the Assertive negotiation style
- The Assertive
- Likes direct communication
- Demands respect
- Gives up only to get more
- Weakest pairing is with the Analyst negotiation style
- The Accommodator
- Focuses on win-win
- Data can be wrong
- Prioritizes communications
- Weakest pairing is with others who have an Accommodator negotiation style
- The Analyst
Another important consideration to keep in mind is that if you’re in security and looking to establish trust, you need to be a collaborator and a bridge builder, not a hero. Rather than being a lone wolf, a collaborator is seen as somebody who others want to work with and won’t be an obstacle to moving things forward and address problems.
Build a security champions team across silos
With an understanding of the domains outlined in the Cynefin framework and the three requirements for establishing trust, the next step is applying key this information in day-to-day work to build trust and break down silos. One important point to keep in mind when establishing trust is that security is there for the business, not to work against it.
Some ways to do so include:
- Identifying and establishing champions in key areas of the business
- Understanding business needs to increase security
- Maintaining regular touchpoints with champions
- Being aware of pitfalls
Develop a risk-aware security program
When looking to build trust and develop a risk-aware security program, the following elements are essential to success.
- Meaningful KPIs and OKRs
- Develop, maintain, and share
- Proxy metrics
- Trusted framework
- Beyond compliance/regulatory
- Catalog of controls vs framework
- Tied to organizational goals
- Recognizes learned risk tolerances
- Varies by business unit
- Varying degree of stressors
- Best practices
- Don’t rely on default configurations
- Continuous and proactive testing
How do you keep trust?
When it comes to establishing and maintaining trust, one thing to keep in mind is that it isn’t a one-size-fits-all strategy and approaches will vary by business.
Once you’ve built trust from a security perspective, a few ways to keep it include:
- Be the organization of “know” not “no”
- Leverage security champions
- Share information bi-directionally
- Learn and use the language of the business
- Maintain, update, and nurture programs and relationships
NetSPI can help you build a trusted healthcare security program
Healthcare facilities and systems have some of the most advanced security programs of any industry, but baseline security measures can only go so far. Four out of five of the world’s largest healthcare companies trust NetSPI to build trust and propel their security programs forward.
NetSPI’s combined technology innovation and human expertise can help your healthcare organization defend against ransomware testing as a service, secure protected healthcare information (PHI) and upgrade medical device security. Learn more about our security services made for healthcare or schedule a demo for additional information.
