
Sky Prioritize Yourself
I’ve covered hacking Passbook files in the past, but I’ve decided that it’s now a good time to cover modifying boarding passes. To start things off, you should not replicate what I’m showing in this blog. Modifying your boarding passes could easily get you in trouble with the TSA, and no one has time for that. iOS 7 has made it a lot easier to export Passbook files, so I think it’s time to point out some issues surrounding boarding passes in Passbook.
First off, let’s send ourselves a copy of a boarding pass. It’s as simple as opening Passbook, opening the pass, and hitting the square in the bottom left corner of the pass.
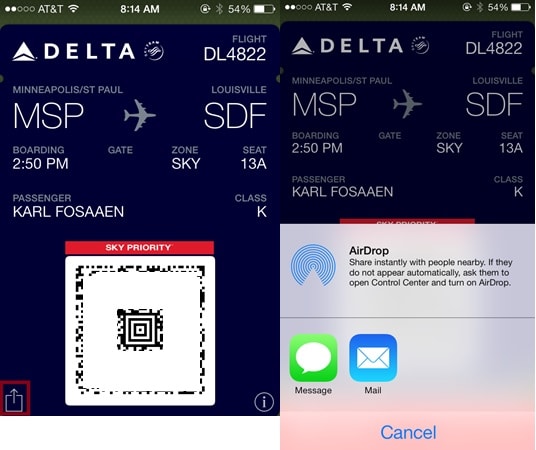
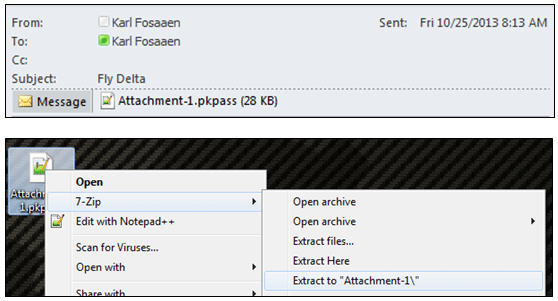
Once you’ve emailed the .pkpass file to yourself, right click on the file and extract (or unzip) the files. The .pkpass file is just a zip file with a different name.
This will result in the following files in the directory.
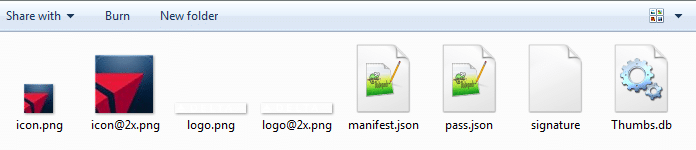
There will be two more files in there if you have Sky Priority. If you don’t already have Sky Priority, the image files can be found here. These footer images are also used for the TSA Pre Check boarding passes. They just have the Pre Check logo appended to the right of the Sky Priority logo.
So we have the boarding pass file. That’s cool. What can we do with it? Well, if you have an Apple Developer’s account ($99 – more info here), you can modify the boarding pass and email it back to yourself. There is a signature file required by iOS to trust the Passbook pass, that can only be generated with a proper Apple Developer’s certificate, but that’s something you get as an Apple developer. I have heard that this signature file is not required for loading Passbook files into the “Passbook for Android” application, but I have not seen it in practice. So if you’re using the passes from an Android phone, there’s a chance that you won’t have to re-sign the pass.
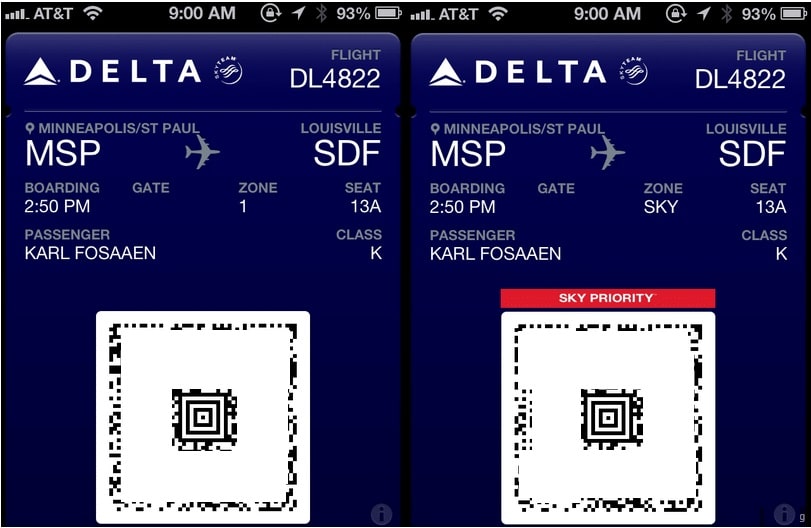
For this demonstration, we’ll show how you can give yourself Sky Priority on a flight. All that you need to do is add the two Sky Priority images (linked above) to your directory and modify the pass.json file to say that you are in the SKY boarding zone. This can easily be done with a text editor. Here’s what my pass.json file looks like after changing the boarding zone.
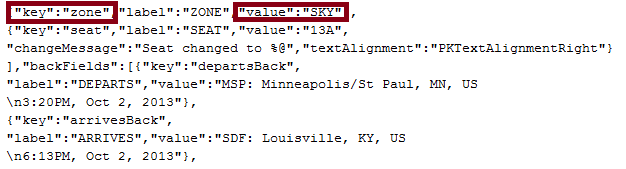
Note that I changed the “zone” parameter. If you felt so inclined, you could change your seat number. If you wanted to social engineer your way into first class, this would be a good way to start. Again, I don’t recommend doing any of this. This would not change your boarding pass barcode (also modifiable in pass.json), which is “tamper evident” and is supposed to be signed by a Delta private key. I have not tested this, but if the airport barcode scanners are not checking the signature, you would be able to modify the barcode as well. Again, I have not tested this or seen it in practice, but I have seen documentation that states the security data (signature) is optional. There’s more info on the barcode standard here.
If you are going to re-sign the pass, you will also need to modify the passTypeIdentifier and teamIdentifier fields (in the pass.json) to match your Apple Developer’s account. If these do not match your Apple info, the pass will not validate when you go to sign and/or use it. There’s some more info on signing your first pass here. You’ll also want to delete your manifest.json and signature files, as those were generated by the original pass signer.
Your final directory will look like this:
At this point you will want to run the SignPass utility on the directory. Your output will look like this.
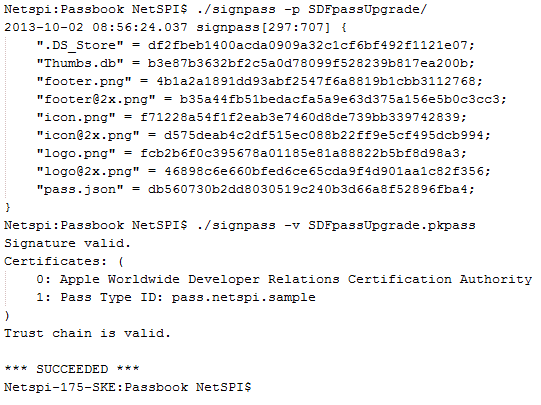
And you will end up with a .pkpass file that you can email to your iOS device.
Now, let’s say you wanted to make it easier to upgrade your priority for all of your flights. It would not be hard to make a script to listen on an email inbox for a .pkpass file, unzip it, modify it, re-sign it, and email the pass back to the sender. On that note, don’t send me your boarding passes. I don’t have this script set up and I don’t want your boarding passes.
This issue is not limited to Delta. Any app that uses Passbook, is vulnerable to pass tampering attacks. This has been a problem for a while. Now that Passbook allows easy exports of .pkpass files, messing with the files is a lot easier.
Explore more blog posts

CTEM Defined: The Fundamentals of Continuous Threat Exposure Management
Learn how continuous threat exposure management (CTEM) boosts cybersecurity with proactive strategies to assess, manage, and reduce risks.

Balancing Security and Usability of Large Language Models: An LLM Benchmarking Framework
Explore the integration of Large Language Models (LLMs) in critical systems and the balance between security and usability with a new LLM benchmarking framework.

From Informational to Critical: Chaining & Elevating Web Vulnerabilities
Learn about administrative access and Remote Code Execution (RCE) exploitation from a recent Web Application Pentest.